Solana absorbed approximately 6 terabits per second of malicious traffic during Breakpoint 2025 in November while maintaining normal block production and transaction confirmation according to infrastructure providers and validator telemetry data. The distributed denial-of-service attack ranked as the fourth-largest publicly reported DDoS event in history and the largest ever documented against a live blockchain network.
The network didn't halt, restart, or require emergency intervention. Validators remained connected, blocks continued every 400 milliseconds, and users completed transactions with sub-second finality throughout the attack. For a blockchain that experienced multiple outages between 2021-2023, this represents structural proof that architectural improvements work under real adversarial conditions.
Attack Scale and Historical Context
The 6 Tbps volumetric attack placed Solana's incident among the most severe traffic floods ever publicly disclosed. According to data compiled by Pipe Network tracking major DDoS events, only three larger attacks have been documented: Google Cloud's 46 Tbps event in 2022, and two Cloudflare customer attacks measuring 38 Tbps and 26 Tbps in 2024 and 2023 respectively.
Microsoft Azure experienced a 3.47 Tbps attack in 2021, while AWS faced a 2.3 Tbps event in 2020. GitHub's 1.35 Tbps attack in 2018 was considered massive at the time. Solana's 6 Tbps incident exceeded all but the three Cloudflare and Google Cloud events in recorded history.
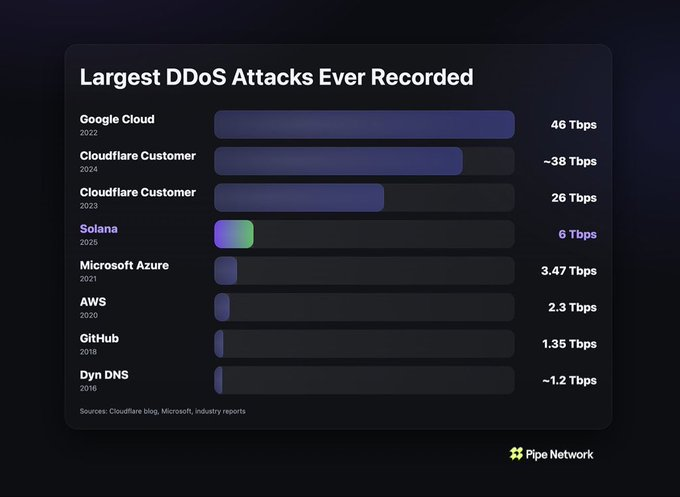
The distinction matters because previous large-scale DDoS attacks targeted centralized cloud infrastructure with extensive redundancy, massive bandwidth reserves, and dedicated DDoS mitigation services. Solana faced comparable traffic while operating as decentralized network with approximately 1,900 validators coordinating consensus across global infrastructure.
Volumetric DDoS attacks flood target networks with massive data volumes designed to overwhelm bandwidth and processing capacity. The 6 Tbps figure represents raw inbound traffic before any filtering or mitigation, creating real stress on validator connections and network coordination.
Why the Attack Didn't Cause Downtime
Solana's resilience during the attack resulted from specific architectural changes implemented between 2023-2025 following previous outage incidents. Four technical improvements directly enabled the network to absorb the traffic without degradation.
QUIC protocol adoption replaced the previous TCP-based networking stack. QUIC provides better congestion control and connection management under packet loss conditions according to Solana Labs engineering documentation. The protocol allows validators to distinguish between legitimate traffic and malformed flood packets without dropping valid connections.
Stake-weighted quality of service prioritizes network traffic based on economic stake rather than treating all connections equally. Validators and staked clients receive priority over unstaked connections, preventing spam traffic from consuming resources needed for consensus according to validator performance analyses published by Solana Foundation.
Local fee markets isolate congestion to specific accounts or smart contracts rather than allowing network-wide slowdowns. When one application faces heavy traffic or spam, fees rise locally for that application without affecting unrelated transactions according to Solana improvement proposals implemented in 2024.
Validator load distribution optimizations improved how traffic spreads across the network. According to validator operator reports, these changes reduced cascading failure risk where one stressed validator could trigger broader network issues during traffic spikes.
Timing Suggests Deliberate Stress Test
The attack occurred during Breakpoint 2025, Solana's flagship annual conference held in Singapore with thousands of attendees and maximum ecosystem visibility. The timing created worst-case scenario for potential network failure from reputational perspective.
During the conference, Solana Foundation and ecosystem projects announced major product launches, enterprise partnerships, and developer tool releases. Network downtime during these announcements would have undermined credibility precisely when ecosystem was demonstrating maturity to institutional audience.
Several infrastructure providers noted the attack's timing appears non-coincidental. Launching volumetric DDoS during quiet period would generate less visibility and might catch network during lower organic traffic. Attacking during peak conference activity created genuine stress test under real operational load.
Whether the timing was targeted or opportunistic remains unclear. But functionally, it provided public demonstration of network resilience under conditions that couldn't be staged or controlled.
What Volumetric DDoS Tests and What It Doesn't
The successful defense against 6 Tbps attack validates specific aspects of Solana's infrastructure while leaving other security properties untested. Understanding these boundaries matters for accurate assessment.
Volumetric DDoS tests network availability under extreme bandwidth stress. It validates that validators can maintain connectivity, coordinate consensus, and process legitimate transactions while absorbing massive malicious traffic. These represent foundational operational requirements for any production blockchain.
However, volumetric attacks don't test consensus safety under Byzantine conditions, smart contract execution vulnerabilities, or cryptographic assumptions. A network can survive DDoS while still containing bugs in virtual machine implementation, consensus algorithms, or application-layer code.
The counterargument is that availability represents necessary but not sufficient condition for blockchain maturity. A network that can't stay online under traffic stress fails before deeper security properties matter. By that standard, Solana demonstrated it cleared the availability threshold under conditions that would have overwhelmed many networks.
How This Changes the Solana Narrative
For three years, Solana's critics pointed to network outages as fundamental evidence that high-throughput blockchains can't operate reliably at scale. The network experienced at least seven significant outages between 2021-2023, including multi-hour downtimes that halted all activity.
These outages created persistent narrative that Solana's architecture made reliability tradeoffs in pursuit of speed. The 6 Tbps incident provides counterevidence: the network absorbed traffic volumes that would have crashed most systems while maintaining normal operations.
The incident doesn't eliminate all concerns about Solana's technical approach. It does invalidate the specific claim that the network can't remain available under extreme stress. That claim was evidence-based following the 2021-2023 outages. It now requires updating based on 2025 performance under documented adversarial conditions.
Broader Implications for Blockchain Infrastructure
Few blockchains have faced comparable stress tests under live conditions. Bitcoin and Ethereum have never experienced publicly documented volumetric attacks exceeding 1 Tbps according to available infrastructure reports. Most Layer 1 networks operate at transaction volumes and public profiles that don't attract sustained multi-terabit attacks.
This creates unusual situation where Solana has more public evidence of availability under extreme stress than networks often considered more conservative in architectural choices. Whether that evidence generalizes to other failure modes remains open question, but it provides concrete data point about one specific dimension of resilience.
Infrastructure providers and validator operators noted the incident demonstrates that decentralized networks can achieve availability properties comparable to major cloud providers when properly architected. This matters for long-term viability of high-throughput blockchain designs.
Why Independent Verification Matters
Claims about network resilience during attacks are easy to make and difficult to verify. Several factors make this incident more credible than typical marketing claims about stress tests or security.
The attack was unplanned and occurred during live event with real-time public observation. Multiple independent infrastructure providers and validator operators confirmed traffic levels and network status throughout the incident. Users continued transacting normally with publicly observable confirmation times remaining sub-second.
No opportunity existed to stage-manage outcomes or control test conditions. The network either worked or failed under conditions visible to thousands of ecosystem participants and external observers monitoring block production in real time.
Solana survived the fourth-largest DDoS attack ever recorded while maintaining normal operations under live conditions during its flagship conference. The architectural changes implemented after 2023 outages proved functional under real adversarial stress rather than theoretical benchmarks.
This doesn't make Solana invulnerable or eliminate other technical risks. It does shift the availability discussion from theory to demonstrated capability. Networks get tested by claims and tested by reality. In November 2025, Solana faced reality at 6 terabits per second and remained operational.
The result won't satisfy critics who focus on different technical concerns. But for the specific question of whether the network can stay online under extreme traffic stress, the answer is now documented rather than debated.




.png)
